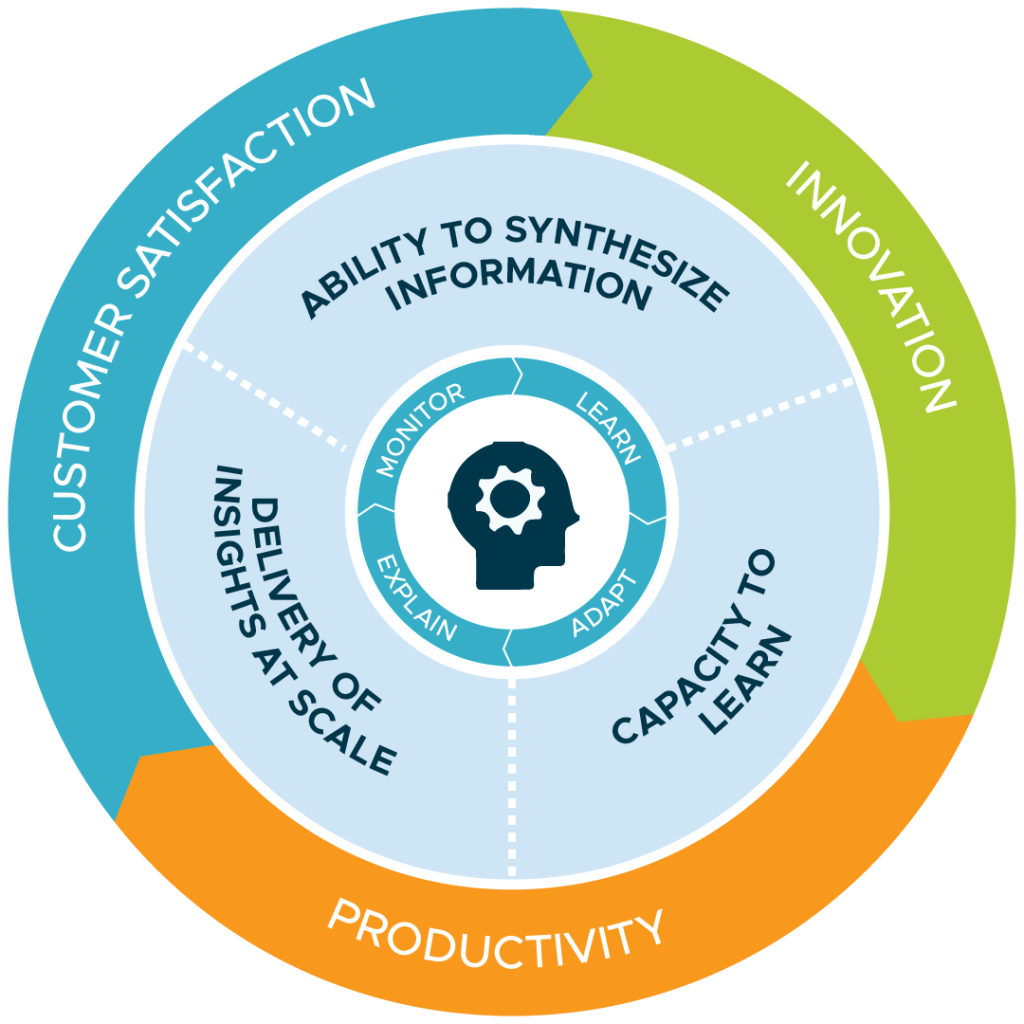
We collect information on crime related activities within the countries we operate through publicly available and national security sources. We synthesize the information to learn and apply the resulting insights at scale to our business operations.
We work closely with customers and stakeholders to ensure we meet customer objectives, transform business security operations, and increase the security program effectiveness to ultimately reduce risk. Every security plan comes with challenges. Our team’s expertise, collaborative approach to planning and controls heads off most problems from the start and provides early warnings on the rest. We’re passionate about creating a sense of certainty from the outset—you can meet your objects with confidence, and without crisis.
We aim for continuous modernization and program management. What does this means? We do not end with the implementation of the security program and services. We employ a modernization mindset that incorporates ongoing operations and maintenance efforts. To this end, we shift the culture from once and done to including a planned refresh cycle periodically whether that’s annually, biennially, or another appropriate timeframe based on a client’s needs. This means checking in with the business to see if goals and objectives have changed and assessed whether the security program supporting that business is achieving desired outcomes. Setting a cadence for revisiting the security plan with stakeholders is key to continuous modernization.
We leverage the use of smart technologies by reverting to the basics and formulating a security plan which incorporates new technologies and techniques that will help support our public spaces. It’s no surprise that risk mitigation options harness new technology designed to create a safer and more secure environment while balancing the facility’s functionality.
The function and level of security of each facility are dependent on the staff, physical characteristics and layout, the location, and the resources available. All of these factors play a critical role in determining what customized technological security solutions can be implemented.
Technology – such as advanced mass notification, social media scrapping, smart cameras or access control associated with facial recognition – allows the facility to leverage its security system to identify and alert the presence of a known, potentially dangerous individual prior to entrance. By utilizing technology to detect, proactively predict and respond to an incident, threat information could potentially be passed simultaneously between staff and local first responders.